✅ What You’ll Need
- PostgreSQL Database (version 9.6 or higher)
- Database Host and Port (usually 5432)
- Database Name
- Admin access to create a read-only user
1️⃣ Create a Read-Only Database User
For security best practices, we recommend creating a dedicated read-only user for Hunch. Connect to your PostgreSQL database as an admin user and run the following SQL commands:Step 1: Create the User
Step 2: Grant Read-Only Permissions
Grant the necessary permissions to access your data: For PostgreSQL v14 and later:Note for Managed PostgreSQL Solutions: If you’re using a managed PostgreSQL service like Supabase, AWS RDS, Google Cloud SQL, or similar platforms, you may need to follow additional steps to create a read-only user.
These platforms often have specific procedures and limitations for user management.
Please refer to your platform’s documentation for the correct method to create a read-only user for your specific managed PostgreSQL instance.
Step 3: Verify the User (Optional)
Test that the read-only user works correctly:2️⃣ Configure SSL (Recommended)
For production databases, we strongly recommend enabling SSL. Configure your PostgreSQL server to require SSL connections.Client SSL Modes
Hunch supports the following SSL modes:require- Always use SSL (recommended for production)verify-ca- Verify the server certificate against CAverify-full- Verify the server certificate and hostnamedisable- No SSL (only for development/testing)
2️⃣ Connect PostgreSQL to Hunch
- Log into Hunch.dev
- Click on your organization name > Connect Data
- Click Configure on the PostgreSQL row
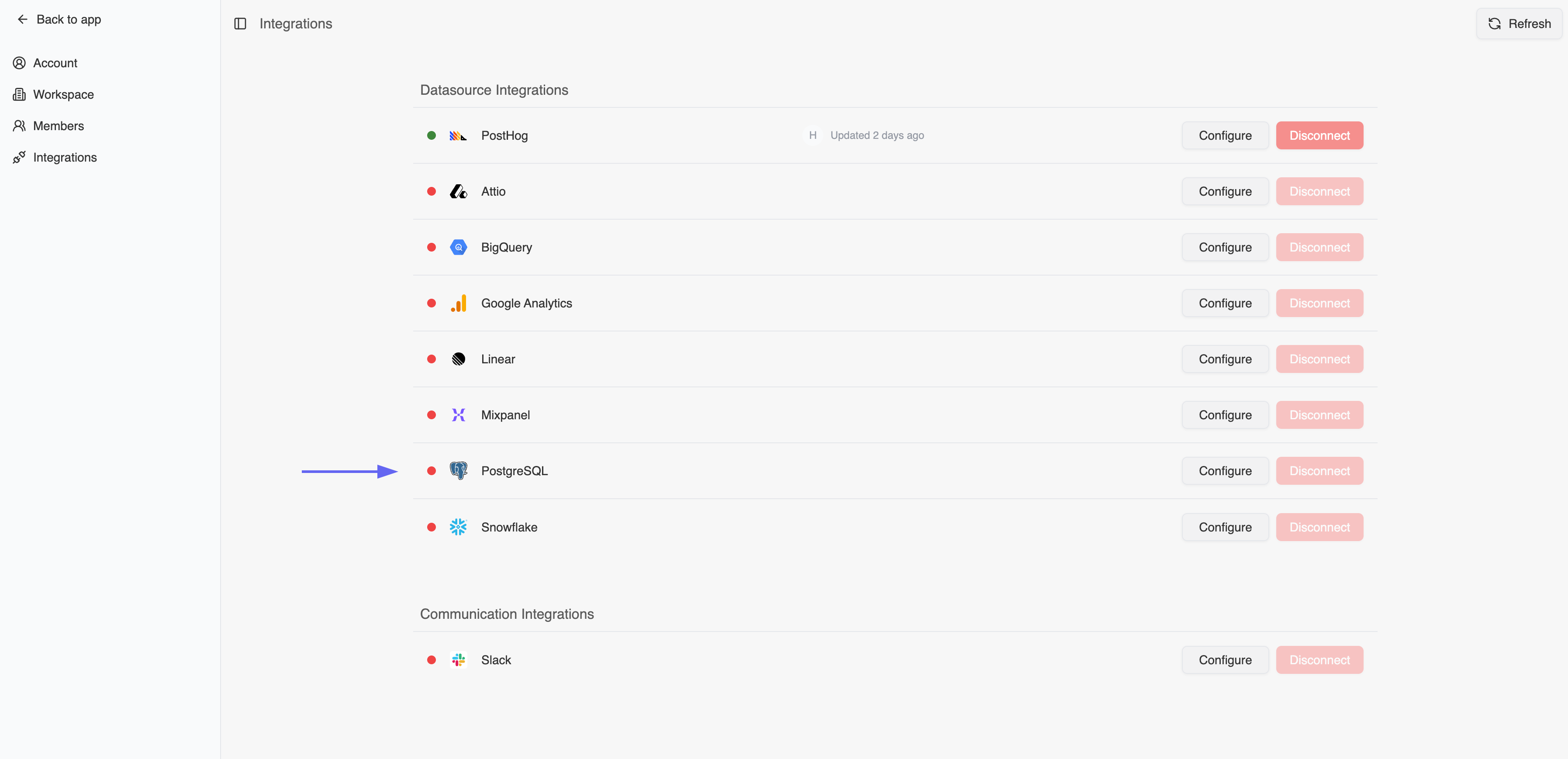
-
Fill in the connection details:
- Host: Your PostgreSQL server hostname or IP address
- Port: Your PostgreSQL port (default: 5432)
- Database: The name of your database
- User: The read-only username you created (e.g.,
hunch_readonly) - Password: The password for the read-only user
- SSL Mode: Select the appropriate SSL mode for your environment
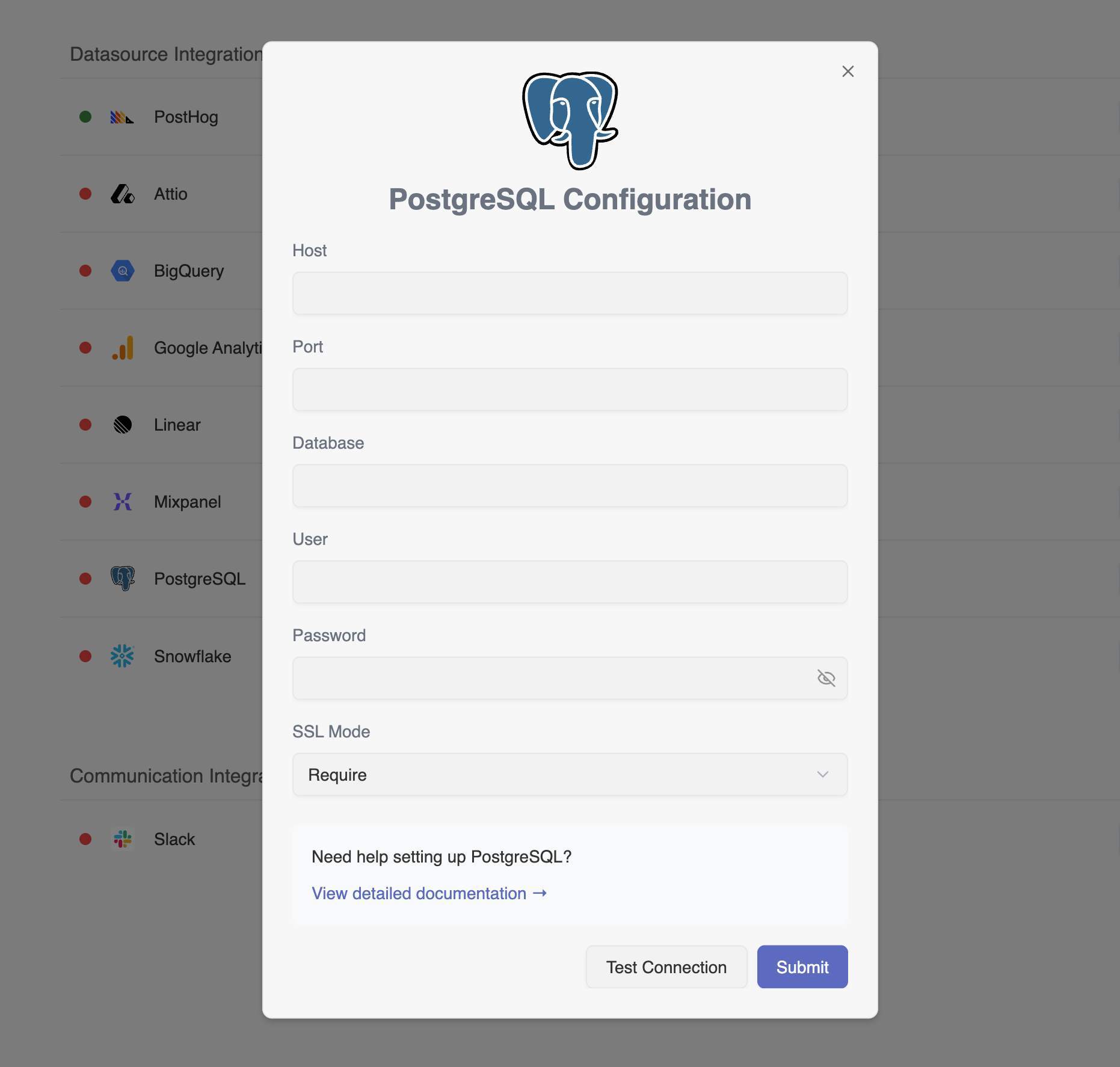
- Click Submit
🎉 Done! You’re now connected
Need help? Ping us at [email protected]🔒 Security Best Practices
Important: Hunch only requires read access to your PostgreSQL data. We recommend:
- Always use a dedicated read-only user (never use admin credentials)
- Enable SSL encryption for production databases
🚨 Troubleshooting
Common Connection Issues
- Connection Refused: Check that PostgreSQL is running and accessible from Hunch’s servers
- Authentication Failed: Verify the username and password are correct
- SSL Connection Error: Ensure your SSL configuration matches the selected SSL mode
- Permission Denied: Verify the user has the necessary permissions on the database and schema